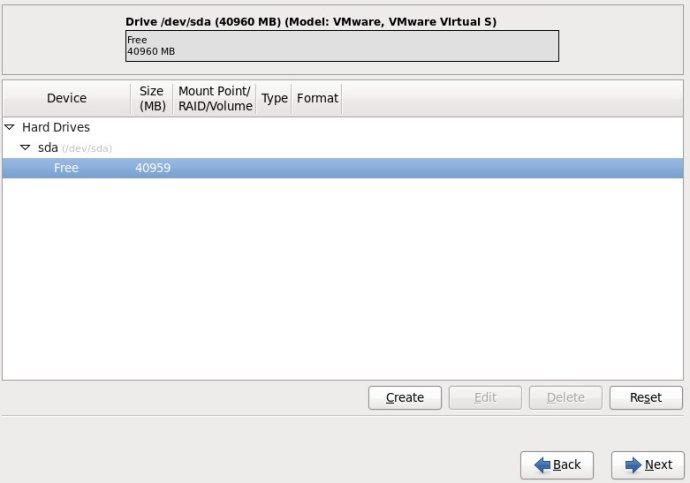
Centos图形创建LVM分区
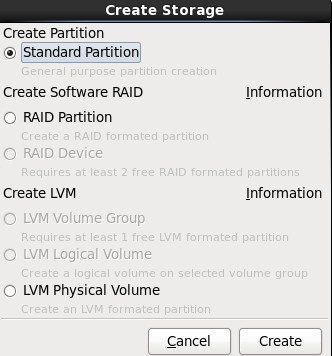
2.选择“Create Partition”选项中的“Standard Partition”,然后点击Create;
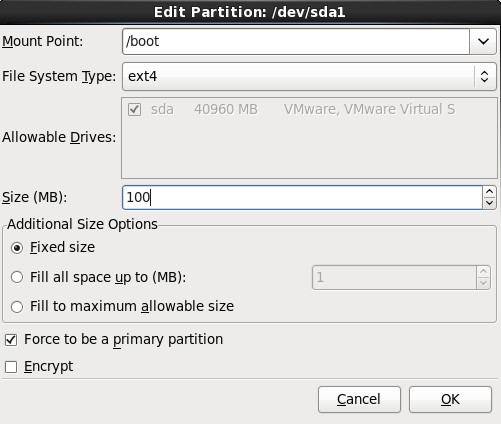
3.在挂载点上选择“/boot”,文件系统类型中选择“ext4”,大小填写100(单位为MB),然后在“Additional Size Options”区域选择“Fixed size”选项,最后再勾选“Force to be a primary partition”,最最后点击OK按钮;
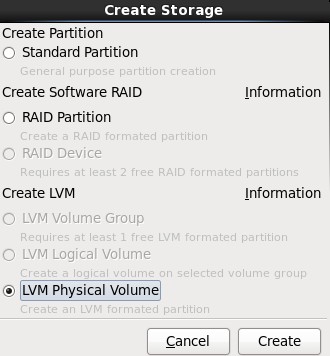
4.选择剩下来的Free行,点击Create按钮,在弹出的对话框中选择“Create LVM”选项中的“LVM Physical Volume”单选按钮,最后单击Create;
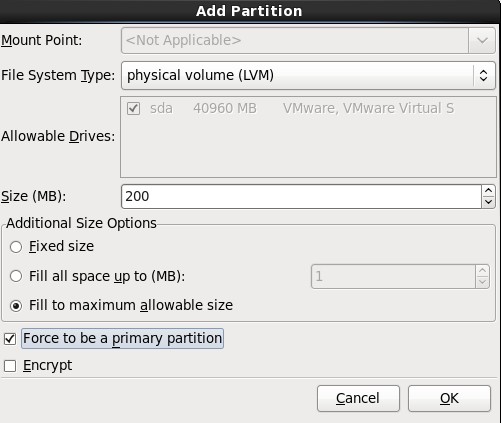
5.在弹出的“Add Partition”对话框中,在“Additional Size Options”区域选择“Force to be a primary size”选项,最后再勾选“Force to be a primary partition”,最最后点击OK按钮;
6.选中sda2这一行,单击“Create”按钮,(千万不要单击“Edit”,不然的话,会回到Standard Partition模式)
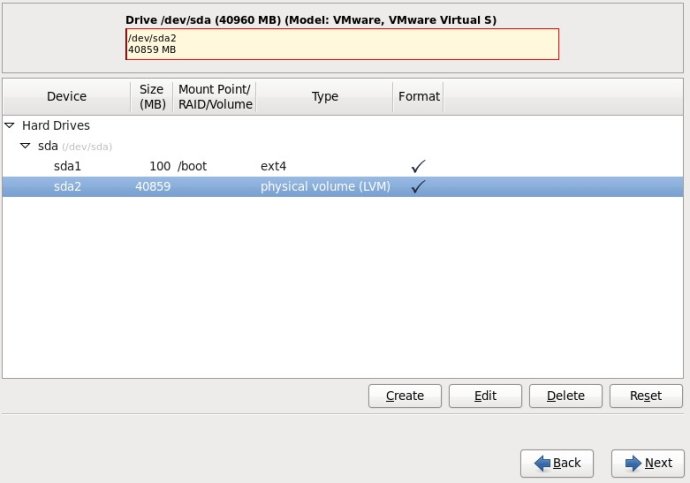
7.在弹出的“Create Storage”对话框中,选择“Create LVM”区域中的“LVM Volume Group”选项,最后单击Create按钮;
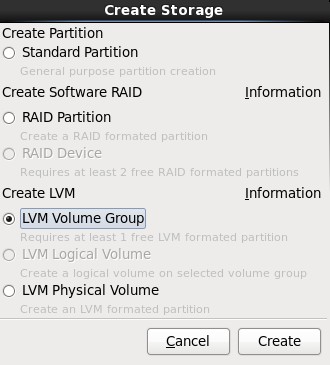
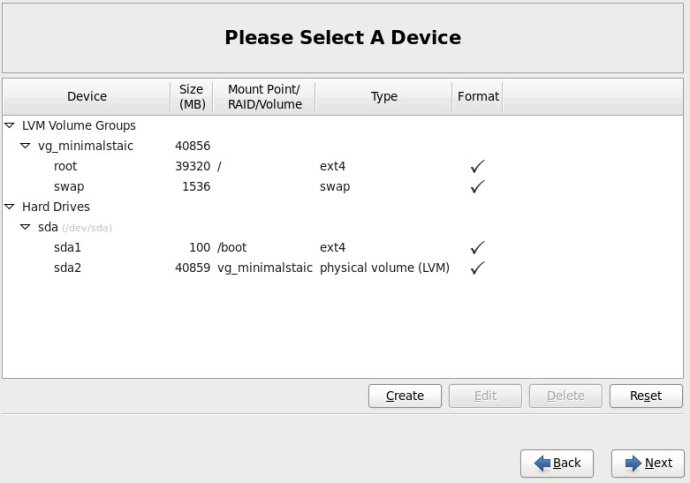
8.在弹出的“Make LVM Volume Group”对话框中,指定“Volume Group Name”的名称(不能包含空格)和“Physical Extent”的大小,默认为4M,最后点击OK按钮;(也可以在这里直接点击Add按钮添加LVM logical Volume)
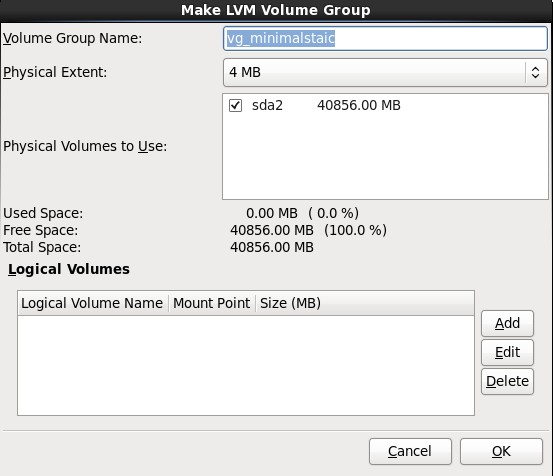
9.单击上图中的Add按钮,在弹出的“Create Storage”中选择“Create LVM”区域中的“LVM Logical Volume”,最后单击Create按钮;
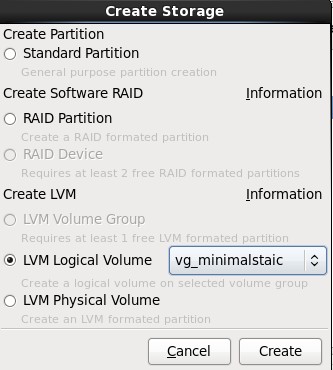
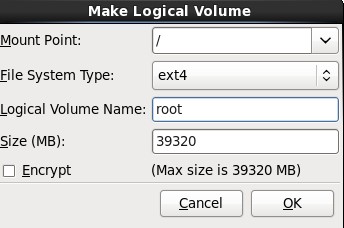
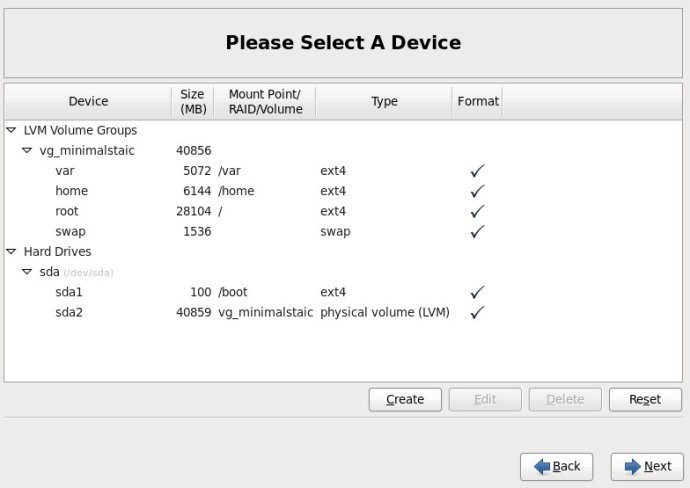
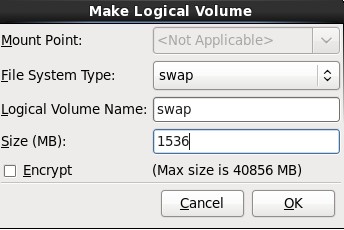
10.在弹出的“Make Logical Volume”对话框中指定挂载点、文件系统类型、逻辑卷的名字和卷的大小,最后单击OK按钮;(如果文件系统类型为swap,则没有挂载点)
参考:http://www.newsky.net.cn/help/Show.asp?id=13